Access Control Overview
Access control lets you create a policy to control who can interact with a resource within the LifeOmic Platform. The LifeOmic Platform uses Attribute Based Access Control (ABAC) to support both simple and complex access control needs.
A simple example of access control is a policy that allows the researcher Julie the permission to create a subject in the vaccine project. Under the ABAC model, the user is performing an action on a resource in an environment. The user, action, resource, and environment all have attributes or key/value pairs. An ABAC policy contains the attributes that define the privileges of the user.
The LifeOmic Platform access control is cumulative. All the permissions granted are allowed. If two permissions grant different levels of access, the most permissive access takes effect.
There are some actions that all users in any group within a LifeOmic Platform account can perform via the API regardless of the ABAC policies in place. Note that these actions cannot be performed via the User Interface and no data associated with any subject is exposed by these actions:
- Read all consents in all projects
- Read all surveys in all projects
- Read all insights layouts, subject viewer layouts, and subject search saved searches
- List all projects including their name and description and other associated metadata
For detailed information on ABAC, see sections 1 and 2 of the NIST's Guide to Attribute Based Access Control.
Default ABAC Policies in Access Control
Each LifeOmic Platform account comes with a standard access control scheme in place. It includes the three basic policies shown below.
| Policy Name | Groups | Permissions |
|---|---|---|
| User Access | Users | Read Data |
| Subject Access | Subjects | Create Data, Read Data, Update Data, and Delete Data restricted to the subject's own data. |
| Administrator Access | Administrator | This policy includes almost all permissions. It does not include Read Masked Data. |
An administrator can start with this default scheme and add additional policies and groups as their organization evolves. If an administrator needs additional permissions not already included in the Administrator Access policy, they have the permissions needed to add to the policy or create a new policy.
To see the default ABAC policies, click the logo at the top of any page to go to the settings page. From the settings page, click Account Info and Access Control.
In the Access Control page Policy Type column, the default ABAC policies and other policies created automatically by the LifeOmic Platform are designated Standard. Custom policies are designated Advanced.
Default ABAC Groups in Access Control
Each default access control policy has a matching group. Adding a user to the group gives the user the permissions from the policy. Users in the Administrators group can update and delete existing groups and policies and create new ones.
- To add an existing LifeOmic Platform user to a group, complete the Add a user to a group with the Users tab.
- To add a new LifeOmic Platform user to a group, complete the Invite a user to a group with email.
Sample Policy
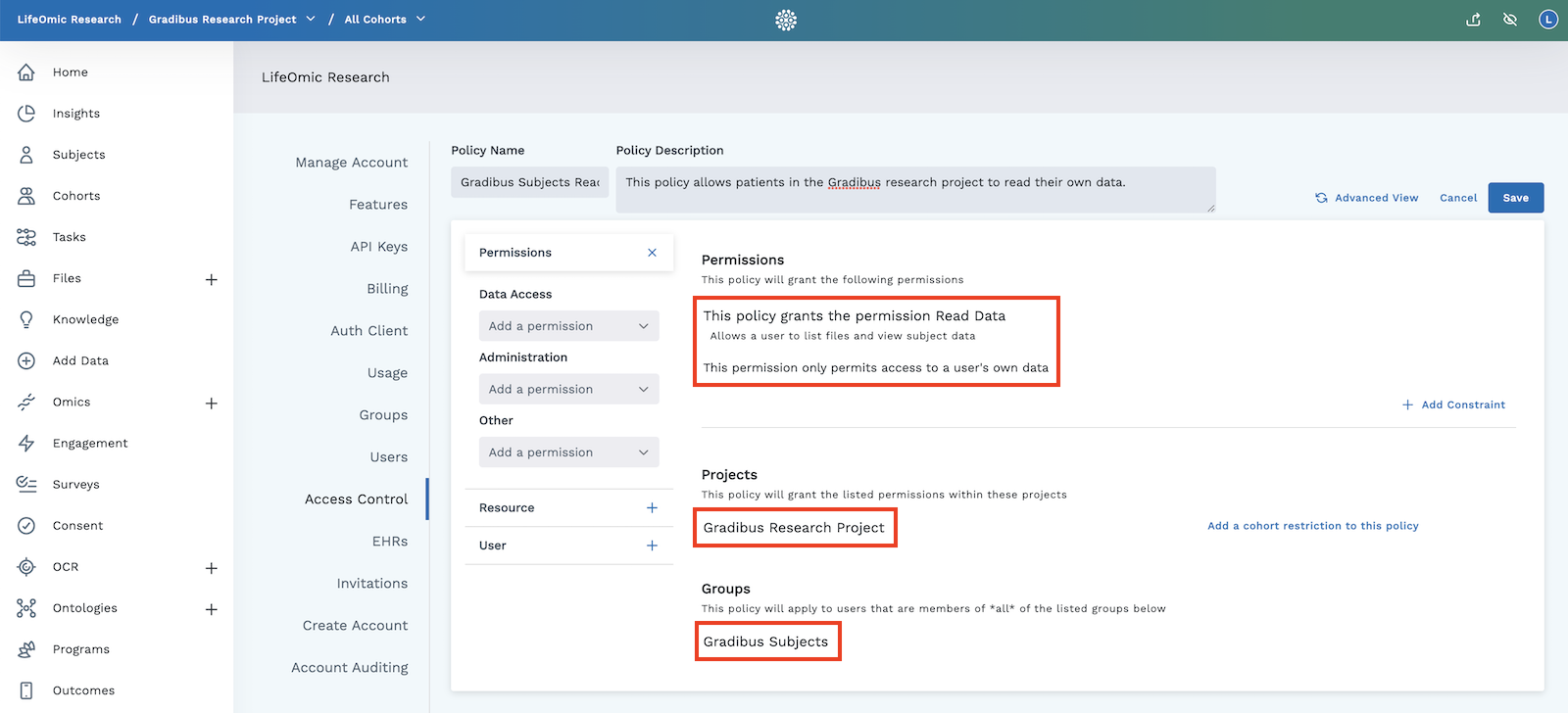
Access control allows you to create custom policies for the specific needs of your project. The example below shows a simple policy designed to allow subjects of a study to read their own data. It contains the three main components required to create a LifeOmic Platform access control policy. These components correspond to the ABAC model.
- Permissions - Permissions are the set of actions allowed by the policy. The only action allowed in the sample policy is to Read Data. This permission is further limited by restricting the policy member's action to their own data.
- Resource - Resource options pertain to the resource being accessed. In the LifeOmic Platform, the resource can be defined by belonging to a specific dataset or by being a specific type of resource. A LifeOmic project is a commonly used resource.
- User - The user specifies which people are members of the policy. Group membership defines these members. In our example, a researcher created the group Gradibus Subjects and sent a LifeOmic Platform group invitation email to the research subjects.
ABAC Tables
The following tables provide information on the LifeOmic Platform access control components. You can see this information in the LifeOmic Platform web app under Account info > Access Control.
Privileges and Permission
| ABAC Privilege | Privilege Name | UI Path | Description |
|---|---|---|---|
| accessAdmin | Administer Access | Permissions > Administration > Access | Allows a user to create, update, and delete groups and policies |
| accountAdmin | Administer Account | Permissions > Administration > Account | Allows a user to update and delete the account, manage auth clients, and configure clinical trial matching. |
| apiKeyUser | Manage API Keys | Permissions > Other > Manage API Keys | Allows a user to create and revoke their API keys for account access |
| billingAdmin | Administer Billing | Permissions > Administration > Billing | Allows a user to manage billing and usage |
| clinicalTrialAlertUser | Manage Clinical Trial Alerts | Permissions > Other > Manage Clinical Trial Alerts | Allows a user to watch clinical trial filters and favorite clinical trials |
| createGenomicData | Create Ingestions | Permissions > Other > Create Genomic Ingestions | Allows a user to view and create genomic ingestions |
| createData | Create Data | Permissions > Data Access > Create Data | Allows a user to add new subject data and files |
| deleteData | Delete Data | Permissions > Data Access > Delete Data | Allows a user to delete subject data and files |
| developApps | Develop Apps | Permissions > Other > Develop Apps | Allows a user to develop and release custom built apps |
| downloadFile | Download File | Permissions > Other > Download File | Allows a user to download file based data |
| engagementAdmin | Administer Engagement Flows | Permissions > Administration > Engagement Flows | Allows a user to configure and add subjects to engagement flows |
| fileAdmin | View Files | Permissions > Other > View Files | Allows a user to view file list and administer file actions |
| ingestFromEHR | Ingest from EHR | Permissions > Other > Ingest from EHR | Allows a user to trigger EHR ingestions |
| inviteUsers | Invite Users | Permissions > Other > Invite Users | Allows a user to send email invitations to other users to join group |
| publishContent | Publish Content | Permissions > Other > Publish Content | Allows a user to publish content to the LifeOmic Platform marketplace |
| layoutAdmin | Administer Layouts | Permissions > Administration > Layout | Allows a user to create, update, and delete subject viewer layouts |
| projectAdmin | Administer Projects | Permissions > Administration > Project | Allows a user to create, update, and delete projects; view, create, and edit gene sets |
| readData | View Data | Permissions > Data Access > Read Data | Allows a user to list files, view subject data, view gene sets, create gene sets, and edit gene sets they've created |
| readMaskedData | View Masked Data Only | Permissions > Data Access > Read Masked Data | Allows a user to list files, view subject data with identifying information masked, view gene sets, create gene sets, and edit gene sets they've created |
| ruleAdmin | Administer Rules | Permissions > Administration > Rules | Allows a user to create, update, and delete rules |
| updateData | Update Data | Permissions > Data Access > Update Data | Allows a user to alter existing subject data and files |
| workflowAdmin | Run Workflows | Permissions > Other > Run Workflows | Allows a user to run workflows and set up workflow based file actions |
Resource Types
You can restrict the Data Access privileges (Create Data, View Data, Update Data and Delete Data) by resource types.
| Resource Type | UI Path | Description |
|---|---|---|
| Insights (insights) | Resource > Resource Type > Insights | Aggregate data that is viewable on the Insights and Subject Search pages; many of the Subject Search filter options |
| Patient | Resource > Resource Type > Patient | Patient demographics Subject Search filters (e.g. name, identifier) and Subject Viewer demographics details |
| Observation | Resource > Resource Type > Observation | Observation data that is viewable on the Subjects page. |
| Condition | Resource > Resource Type > Condition | Condition data that is viewable on the Subjects page. |
| Procedure | Resource > Resource Type > Procedure | Procedure data that is viewable on the Subjects page. |
| Cohort | Resource > Resource Type > Cohort | Cohort data that is viewable on the Cohorts page or Subject Search |
| GeneSet | Resource > Resource Type > Gene Set | Gene set data that is viewable on the Knowledge, Subject Search and Omics Explorer pages |
| Questionnaire | Resource > Resource Type > Questionnaire | Surveys configured on the Surveys page, consent terms configured on the Consents page, and FHIR Questionnaire resources |
| QuestionnaireResponse | Resource > Resource Type > Questionnaire Response | Survey responses completed by subjects and FHIR Questionnaire Response resources |
| Consent | Resource > Resource Type > Consent | Consent agreement completed by a subject and general FHIR Consent resources |
| Terminology | Resource > Resource Type > Terminology | Ontology and terminology data used in Subject Search filters, Insights layouts and Subject Viewer layouts |
| job | NA | Granting Create Data access to this resource type allows a user to run bulk actions in Subject Search such as assigning surveys |
| FHIR Resource Types | NA | All FHIR resource types supported by the LifeOmic Platform, including: Observation, Condition, Procedure, and others.. |
| Data Lake | Resource > Resource Type > Data Lake | Result files created by running data-lake queries |